Using the logs that Windows writes, you can get information about which IPs and which users connected to the virtual server, and when they did it.
The instructions below can be used on desktop versions of Windows as well.
Let's take a look at some of the most common codes associated with server startup and shutdown times.
1149: The presence of this code indicates successful user authentication on the server. (Remote Desktop Services: User authentication succeeded)
21: this code indicates a successful login, that is, the user saw the desktop window. (Remote Desktop Services: Session logon succeeded)
24: This event indicates a successful disconnect from RDP (Remote Desktop Services: Session has been disconnected)
25: indicates reconnection to the RDP session. (Remote Desktop Services: Session reconnect succeeded)
23: user pressed Logoff and logged out (Remote Desktop Services: Session logoff succeeded )
39: The user personally logged out of the RDP session (not just closed the RDP window). Or it was disabled by another user or administrator.
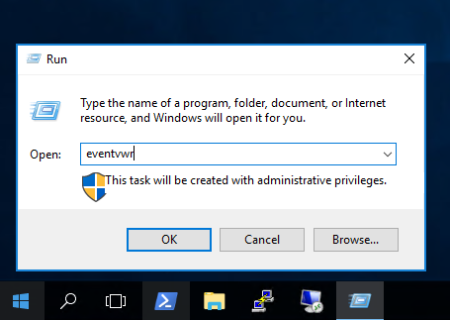
How to view event data?
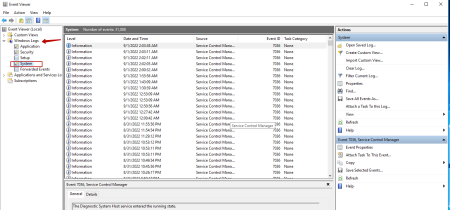
Press Win+R and type eventvwrOn the left side of the panel, open "Windows Logs => System"
In the Event ID column, we will see a list of events that occurred while Windows was running. The event log can be sorted by event ID.
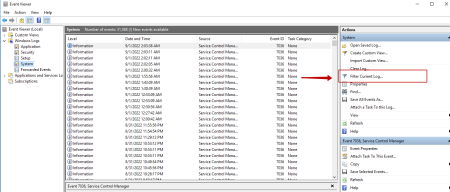
In order to sort the events we need, on the right side, select "Filter the current log"
Now enter the events we need, separated by commas, 1149,39,25,24,23,21 and click OK.
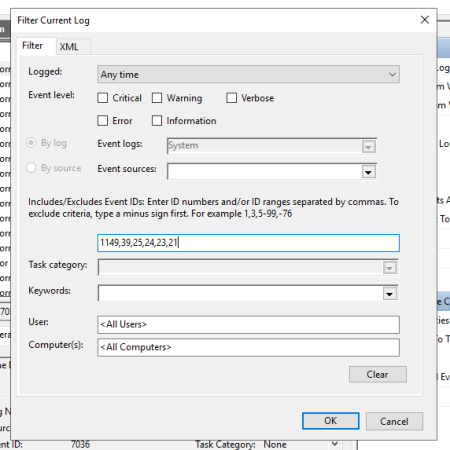
Now we can observe the event log with the shutdown of our VPS server.
These events can be viewed in different sections. For example:
EventId 1149,4624,4625 - filtering in Windows Logs => Security
EventId 25,24,21,39 - filter in Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational
EventId 23 - Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational
Now you can independently check by who and when RDP accessed your server.