The main reason why there is a need to organize a single point of access to a fleet of Windows servers is security. In addition, it will provide convenient administration and control of access to remote desktops. This is especially true if there are many remote employees who connect to servers from different IPs and these IPs often (or sometimes) change.
Description. The role of a single access point will be performed by RouterOS installed on a separate virtual server. To connect to the server, the user will specify the IP of the server hosting RouterOS and the connection port. The organization of redirection to the desired server will be taken over by the NAT rules created in the Firewall RouterOS. On Windows Server, let's set permission to access via RDP only from the IP of the RouterOS server, thus ensuring its security.
The big advantage is that for granting access, restriction and control, the administrator can use all the advantages of the RouterOS system.
Let's get started.
First, install and configure RouterOS on a virtual server.
To install RouterOS, follow the instruction "How to install RouterOS on a virtual server (VPS/VDS)"
Next, let's set it up. For our task, it will be enough to carry out basic RouterOS security settings.
For this:
1. Connect to RouterOS using the WinBox program (you can download the program on the Mikrotik official website)
2. Add DNS. Needed to check and install updates.
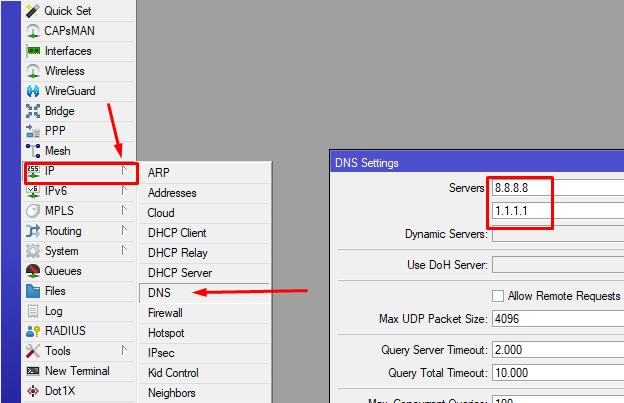
3. Disable all RouterOS services that are unnecessary for our task, except for WinBox
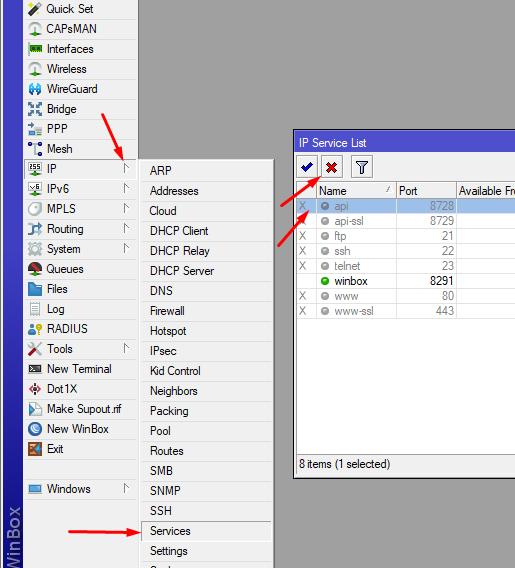
4. In the IP - Routes menu, check for a default route. As a rule, the route should already be created after configuring the network interfaces.
5. Add basic firewall security settings.
5.1 Let's allow established and related connections:
IP -> Firewall -> Filter Rules -> + -> General: Chain=input, Connection state=established,related; Action: Action=accept; Comment="Trusted"
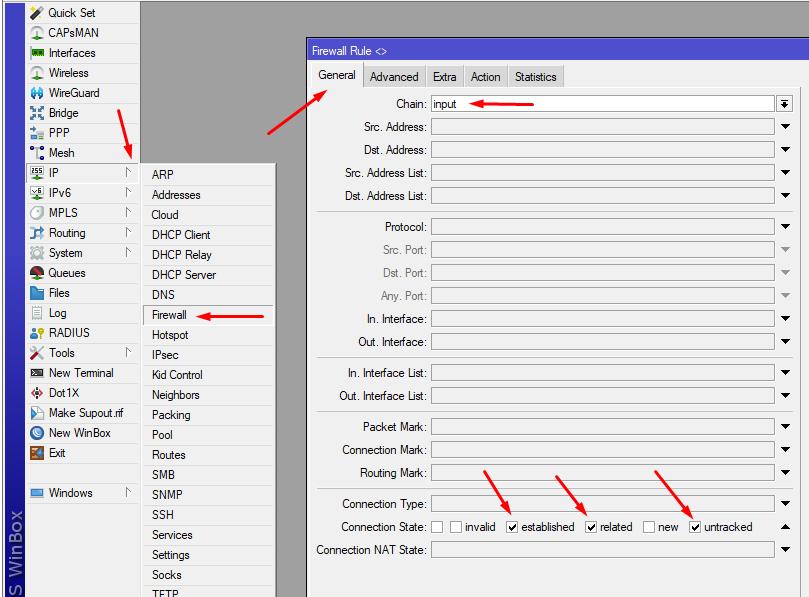
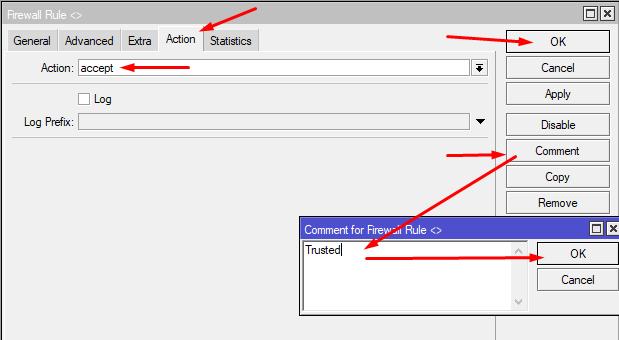
5.2 Prohibit invalid connections:
IP -> Firewall -> Filter Rules -> + -> General: Chain=input, Connection state=invalid; Action: Action=drop; Comment="Drop Invalid Packet"
5.3 Let's create a blocking rule for IPs from which connection attempts are made to well-known ports. IP will be blacklisted for 10 hours (any time can be set)
To speed up task creation, open a new terminal (New Terminal)
and sequentially copy, paste and run the commands:
ip firewall raw add chain=prerouting src-address-list=BlackList action=drop comment="BlackList"
ip firewall filter add action=add-src-to-address-list address-list=BlackList address-list-timeout=10h chain=input protocol=tcp connection-state=new dst-port=20-25,80,110,161,443,445,3128,3306,3333,3389,7547,8080-8082 comment="Add to BlackList TCP port scanning"
Execution results
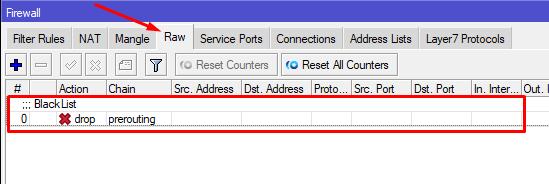
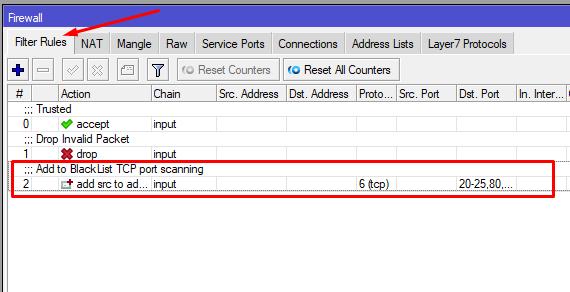
By the way, after a short time, IPs from which there were attempts to connect to RouterOS via a public port will appear in the BlackList. The list of blocked IPs is available in the Address Lists tab
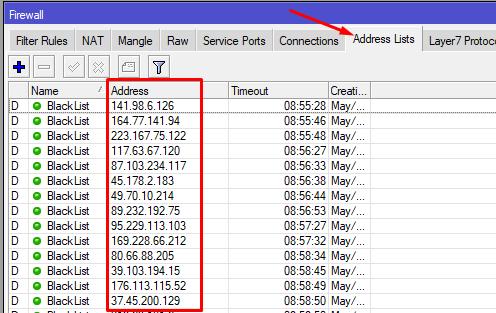
This completes the RouterOS basic protection setup.
6. Now we will configure port forwarding on RouterOS so that connections to a specific RouterOS port are redirected through RouttrOS to the Windows server.
6.1 Let's add a rule (masquerading rule) that provides address substitution for the destination of packets that come from the server. This will allow packets on established connections to seamlessly pass RouterOS from the server to the user's computer. This single rule will "forward" all packets from all servers.
IP - Firewall - NAT - +
General: Chain = srcnat
Action: Action = masquerade
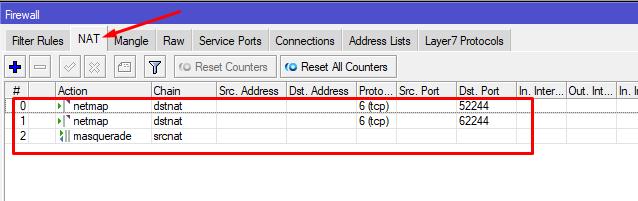
6.2 Let's add a rule that provides a connection to a specific server.
IP - Firewall - NAT - +
General: Chain=dstnat, Protocol=6(tcp), Dst.Port=52244
Action: Action=netmap, To Addresses=SERVER_IP, To Port=3389
Note two meanings.
52244 is the port number that must be specified when connecting to the server. The number can be set in the range 1024-65535
SERVER_IP is the real IP of the server to connect to.
Should look like this:
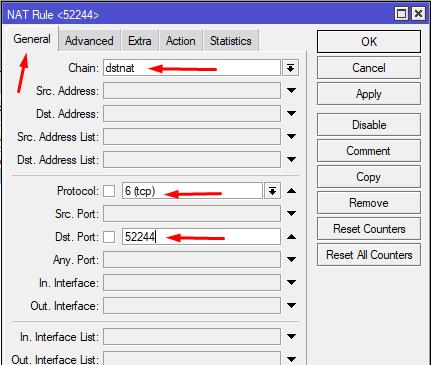
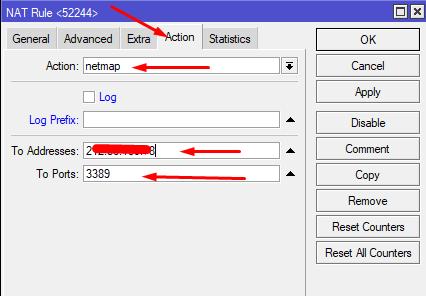
You can also check the Log checkbox and set the Log Prefix value so that you can see the connection specifically to this server in the RouterOS log (Log menu).
To create a connection to another server, create the same dstnat rule, specifying the IP of another server and a different port number (for example, 62244).
In this case, the masquerading rule should be one.
This completes the RouterOS setup.
Now let's allow access on the Windows server only from the IP hosting RouterOS. To do this, use the instructions "Как предоставить доступ к Windows Server по IP или диапазону IP"
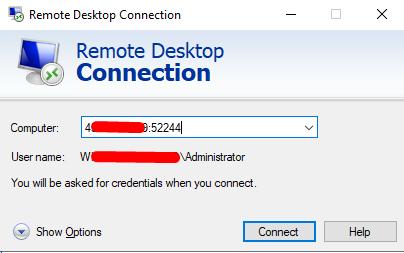
Check the connection to the server by specifying in the Computer field
IP_RouterOS:52244
where
IP RouterOS - IP of the server hosting RouterOS
52244 - port for connecting to the first server
To connect to the second server, specify in the Computer field
IP_RouterOS:62244
Thus, we have learned how to create a system for connecting to Windows servers through one IP address.

