Fail2ban — is a well-known intrusion detection system for Linux. It analyzes log files to detect automated attacks and failed login attempts. By identifying the IP address from which the attack is coming, Fail2ban instantly blocks it, making this system indispensable in the fight against brute-force attacks. Installing and configuring Fail2ban is a simple process. Here's how to install Fail2ban on CentOS 7.
- Update CentOS
Run the terminal and update your CentOS system by running the following commands.
yum update -y yum upgrade -y
-
Install fail2ban
To install fail2ban, run the following command.
yum install epel-release yum install -y fail2ban
- Start and activate Fail2ban
Turn on and activate fail2ban using the following commands.
systemctl start fail2ban systemctl enable fail2ban
The status of fail2ban can be checked with this command:
systemctl status fail2ban
-
Fail2ban Setup
Fail2ban uses 4 configuration files. They are read in the following order:
/etc/fail2ban/jail.conf /etc/fail2ban/jail.d/.conf /etc/fail2ban/jail.local
Most users copy the default jail.conf file to jail.local and modify it. Let's do this:
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Open jail.local with a text editor:
vim /etc/fail2ban/jail.local
You'll find different sections in this file, each with detailed comments about its purpose.
Let's look at the main settings:
-
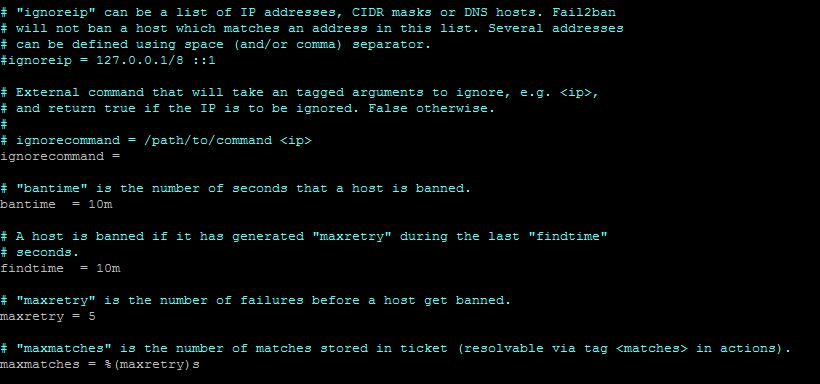
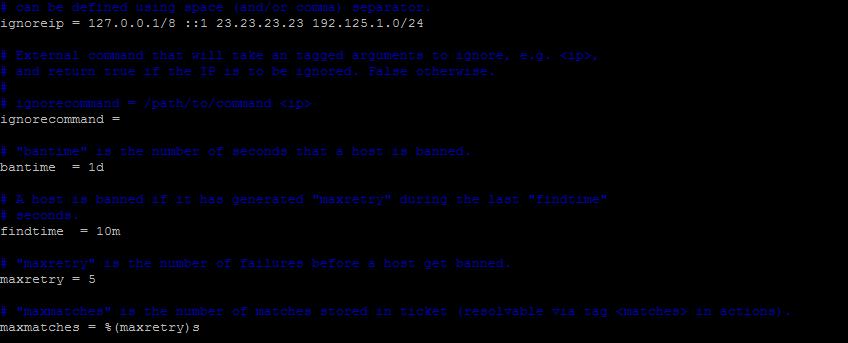
ignoreip — used to specify IP addresses that should not be blocked. To add one or more IP addresses, uncomment the line that starts with ignoreip and add IP addresses separated by commas. Here is an example.
ignoreip = 127.0.0.1/8 ::1 23.23.23.23 192.125.1.0/24
-
bantime — blocking time. By default — 10 minutes. To set it to 1 day, do the following:
bantime = 1d
-
findtime — the time during which the specified number of failures or attacks should occur. If you have configured fail2ban to block IPs after 3 failed attempts, those attempts should occur within the findtime value. Example:
findtime = 10m
-
maxretry — the maximum number of failed attempts before the IP is blocked. Example:
maxretry = 5
Test and unblock the IP address
.
Try logging in to your server via SSH, entering the wrong data each time. You will not be allowed to connect to your server via SSH after the third unsuccessful login attempt.
Fail2ban has a built-in client that allows you to control the service. It can be used to remove blocking from an IP address.
For example, you need to block a user's IP who keeps breaking into the server.
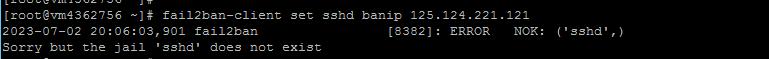
To block an IP address (for example, 125.124.221.121), use the command:
fail2ban-client set sshd banip 125.124.221.121
If you get this error message fail2ban [7825]: ERROR NOK: ('sshd',), Sorry but the jail 'sshd' does not exist - , this indicates that Fail2ban cannot find the 'sshd' configuration. The &#quot;jail" in Fail2ban are rule sets for various services that Fail2ban should monitor, such as ssh, apache and others.
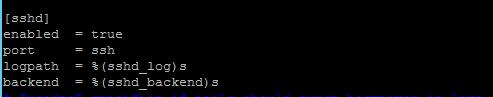
First, you need to check the Fail2ban configuration file (usually '/etc/fail2ban/jail.conf' or '/etc/fail2ban/jail.local') and make sure it has a section for 'sshd'. It should look something like this:
[sshd] enabled = true port = ssh logpath = %(sshd_log)s backend = %(sshd_backend)s
After making any changes to the configuration file, the Fail2ban service should be restarted with the command:
sudo systemctl restart fail2ban
The command to block the IP address should now work without errors.
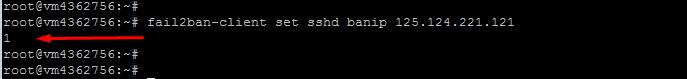
If you want to remove the blocking from an IP address (for example, 125.124.221.121), do the following command:
fail2ban-client set sshd unbanip 125.124.221.121
In conclusion, Fail2ban is an effective intrusion detection tool which blocks the IP addresses from which repeated failed login attempts are coming from. It plays a key role in keeping your Linux systems secure, whether CentOS 7 or Ubuntu.
In this article, you can easily install and configure Fail2ban on your servers. In addition to installing and enabling Fail2ban, you'll also learn how to configure IP blocking settings, check the status of the service, and manage the blocking of individual IPs.

