In today's world, where the Internet is an integral part of our lives, setting up computer system protection is an extremely important task. One of the ways to protect a computer system is to configure the Firewall. In this article, we will look at how to set up Firewall using IPTables on CentOS 7.
IPTables is a Linux utility that is used to configure the Firewall. IPTables is a networking stack that filters packets passing through the system. IPTables works at the kernel level and filters packets before they reach user space.
IPTables has three main chains: INPUT, OUTPUT and FORWARD. The INPUT chain is used to filter packets directed to the system. The OUTPUT chain is used to filter packets sent from the system. The FORWARD chain is used to filter packets passing through the system.
Following are the basic commands for working with IPTables. Note that each command must start with sudo, as changing IPTables settings requires superuser privileges.
Creating a new chain:
sudo iptables -N <chain_name>Removing a chain:
sudo iptables -X <chain_name>Adding a packet filtering rule:
sudo iptables -A <chainname> -p <protocol> --dport <port> -j <target>Removing a rule:
sudo iptables -D <chain_name> <rule_number>Viewing the list of rules:
sudo iptables -L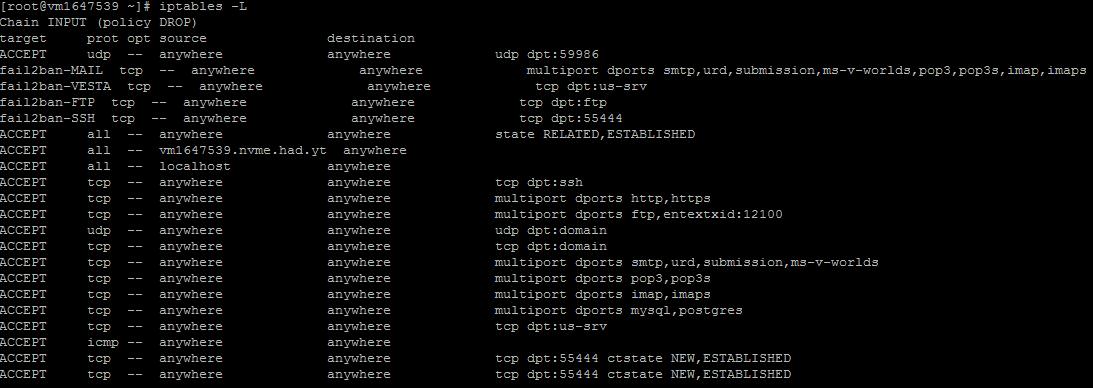
Saving rules:
sudo service iptables save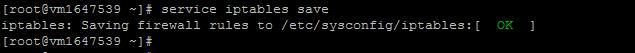
An example of configuring Firewall using IPTables on CentOS 7:
Let's say we have a server running CentOS 7 and we want to configure the Firewall to block all incoming packets except SSH, HTTP and HTTPS.
Create a new chain to block all incoming packets:
sudo iptables -N INPUT_BLOCK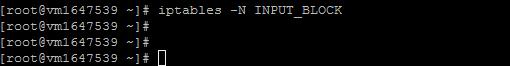
Adding rules to block all incoming packets except SSH, HTTP and HTTPS:
sudo iptables -A INPUT_BLOCK -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A INPUT_BLOCK -p tcp --dport 22 -j ACCEPT
sudo iptables -A INPUT_BLOCK -p tcp --dport 80 -j ACCEPT
sudo iptables - A INPUT_BLOCK -p tcp --dport 443 -j ACCEPT
sudo iptables -A INPUT_BLOCK -j DROP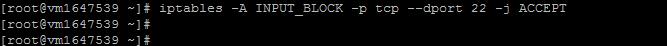
Adding rules to allow outgoing packets:
sudo iptables -A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A OUTPUT -j ACCEPT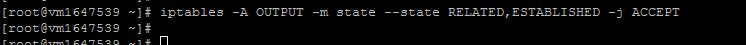
Adding rules for packet forwarding (if required):
sudo iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A FORWARD -j DROP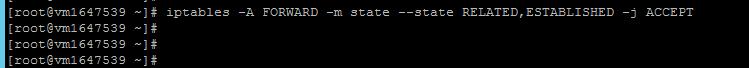
Apply settings:
sudo service iptables save
sudo systemctl restart iptables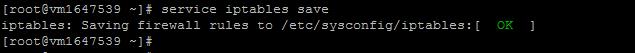
This is an IPTables setting that blocks all incoming packets except SSH, HTTP, and HTTPS, allows outgoing packets, and does not allow packet forwarding.
In conclusion, configuring the Firewall with IPTables is an important task to ensure the security of a computer system. IPTables provides a wide range of options for configuring the Firewall, and knowledge of its commands and configuration files allows you to effectively protect your computer system. But remember that any changes you make will be instantly applied to your Firewall, which may affect your current network connections. Be careful and always have an up-to-date copy of your settings before making any changes.

